We’re tracing the lines of mobile attack
Uncompromising Mobile Threat Defence for business
We believe that privacy is a human right. And we believe that every business deserves to be free from the fear and threat of cybercrime. So we made a Mobile Threat Defence system with amazing protection, without compromising privacy.
Try Trustd MTD for free Schedule a demo
(Get started in under 1 minute!)
Deeply clever protection
The AI-powered protection in Trustd is built for the needs of mobile users by mobile security specialists. It stops malware and phishing attacks that have never been seen before, WiFi protection identifies malicious or insecure hotspots, and our privacy protection stops cameras, mics or messages being accessed without consent.
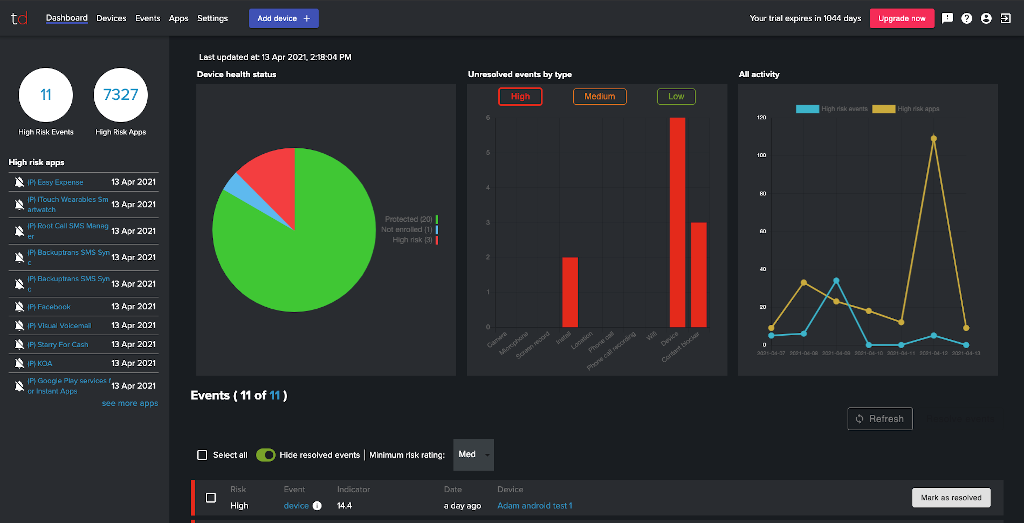
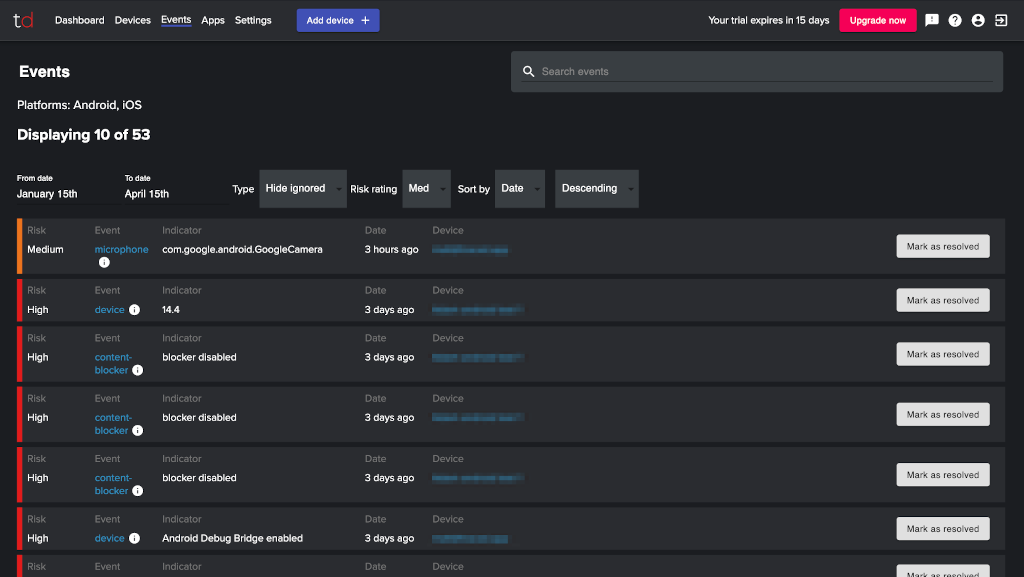
Privacy-first design
Privacy has been built into our products from the start, so your employees know they’re being protected, not tracked, and you know your business is secure from cyberthreats, and safe from unexpected data protection issues.
Better value
We wanted to build a mobile security product that would protect everyone. So we made our consumer app free, and our Trustd Mobile Threat Defence for businesses is the lowest possible price we can sustain – less than half the price of other mobile security solutions.
The story so far
Traced is a young company that’s growing fast and have already protected over 250,000 mobile devices. Join us on our journey.
“We found the missing piece of the jigsaw for our mobile devices”
Kirk Croal, Technology Director, Huntswood. Read the case study.
Recent awards



Praise for our protection
- “What Traced are doing is really important. Enabling corporate protection whilst being respectful of employees’ right to privacy”
- “Seconds to install, complete peace of mind”
- “I’d recommend this over and over again”
- “Offers peace of mind to my privacy”
- “Took seconds to set up”
Get the Trustd app for free
The Trustd app protects your mobile device from app, network and device-based threats like malware, phishing, rogue WiFi; from unauthorised screen, camera and mic access; and from permissions abuse and device exploits.
It is available for free from Google Play and the App Store.