How privacy-friendly mobile security keeps your business data safe

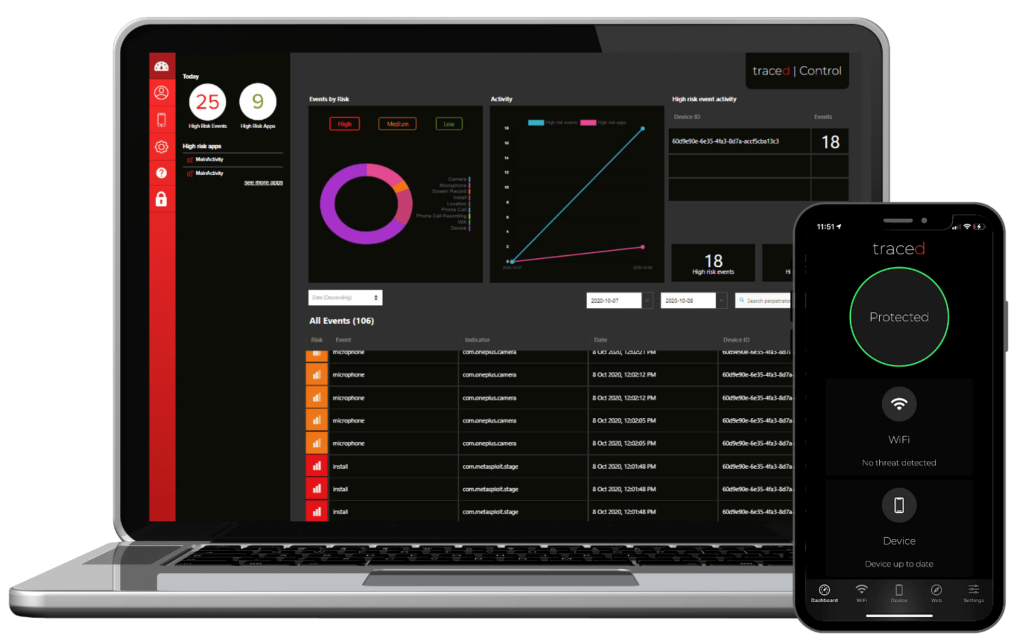
See and secure every device
You need productivity, so whether you provide a corporate-owned mobile device to staff or you allow employees to use personal mobile devices at work, you need to protect the confidential and personal data stored on and accessed by those devices. Your mobile security program needs to be sustainable and every single device needs to be accounted for. If even one unsecured device is used to access business data you put yourself at risk of a data breach.
Stay compliant, reduce risk, and protect every device.
Phishing attacks and ransomware are the prime causes of data loss for businesses. Humans are the weakest link in the security chain, and despite regular security training, employees regularly fall for scams, click links to malicious websites, connect to compromised WiFi networks, or install dangerous apps. You need to ensure every device is protected, including mobiles and tablets where small screens and distractions often cause security slip ups.
85% of mobile phishing attacks are delivered outside of email
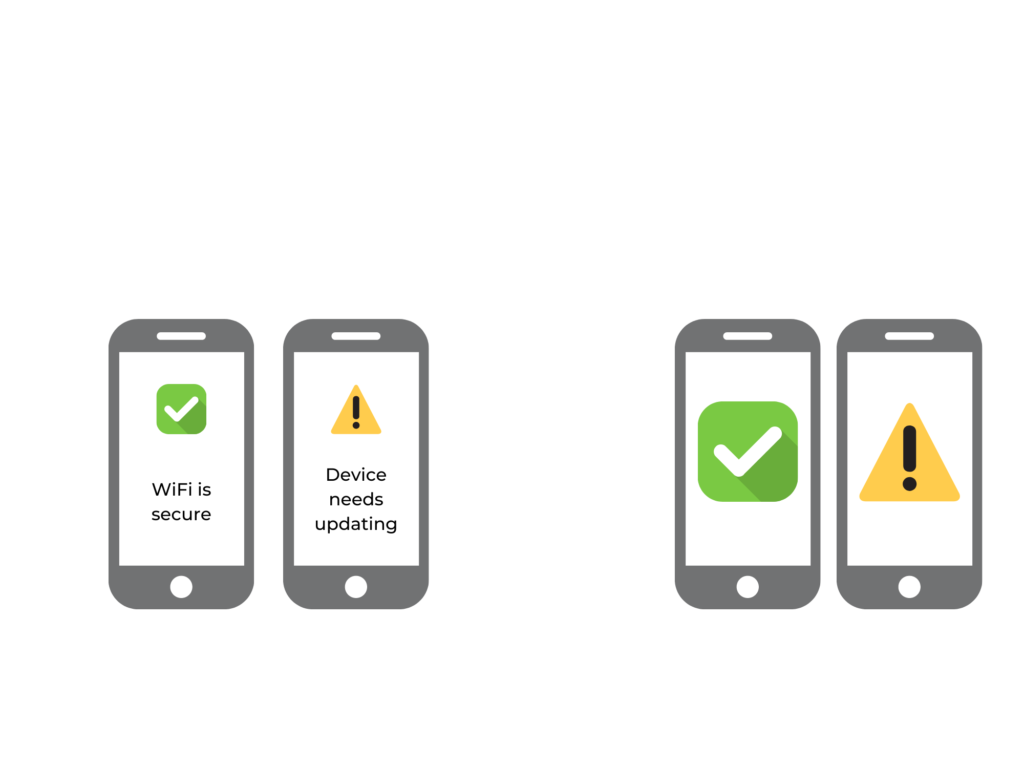
Comparing mobile security solutions.
Mobile Device Management (MDM) software is a common solution in place in larger organisations to protect mobile devices. However, as well as not providing threat detection and remediation, it necessitates employees opening up access to their personal phone or tablet to management by their employer – who have the ability to install and manage apps, remove apps, revoke access to apps or email etc.
Mobile Threat Defence (MTD) software set out to solve the threat detection and remediation issues in MDM. It’s less intrusive than MDM, but it’s relatively new on the security scene and employees are still understandably wary of potentially invasive software on their devices. Traced Control is an MTD that puts employee privacy first, while allowing organisations the peace of mind that comes from seeing that every device is secure and protected against phishing, malicious apps and content, malware, attacks over unsecured WiFi, and device configuration vulnerabilities.
Video: See how Traced Control protects data on mobile devices.
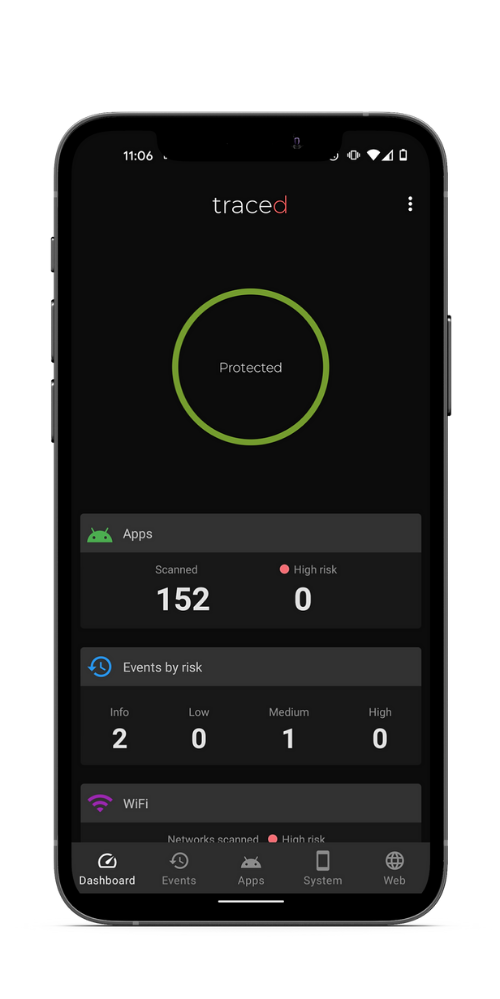
Unparalleled protection
The Traced app on employee mobile devices protects them from application, network and device-based threats including malware, phishing, rogue WiFi, unauthorised screen, camera and microphone access, permissions abuse and device exploits.
The Traced Deep Learning engine detects both known and unknown malicious apps and provides you with crucial information for your analysis, investigation and response.
Traced guides the device user to remediate threats, while alerting IT admins in real time about the threats. When the user resolves the issue, the threat is downgraded. Security teams know mobile devices are protected; IT compliance and governance teams know every mobile device is enrolled and actively using company security policies; and employees know that their personal information and activity remains completely private.
Try it for yourself
Traced Control is a new mobile threat defence solution that is quick and simple to set up – see for yourself with our 14-day free trial. Get set up in 5 minutes and enrol your own devices to see the process, and explore Control. If you’re looking for our free app, head over here.