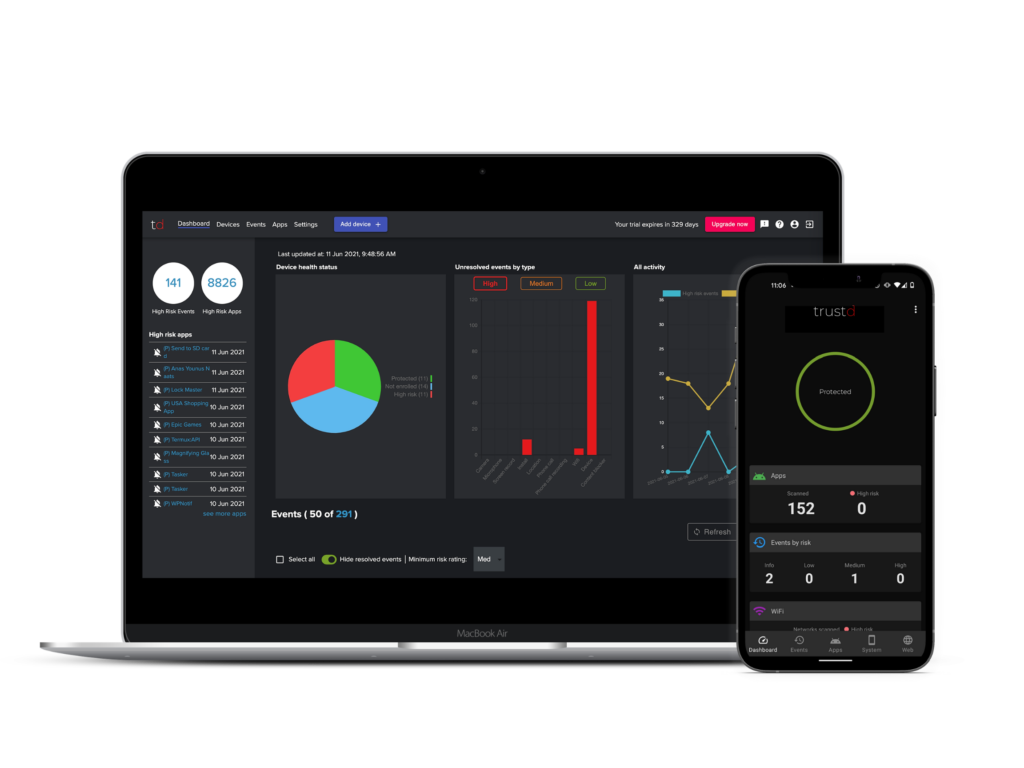
Remember when the only threats you had to worry about were on your computer?
Those days are over. If an employee falls victim of a mobile phishing attack it can have serious implications. Compromised data can be used for credential stuffing and identity theft, resulting in the fraudulent access of your business systems.
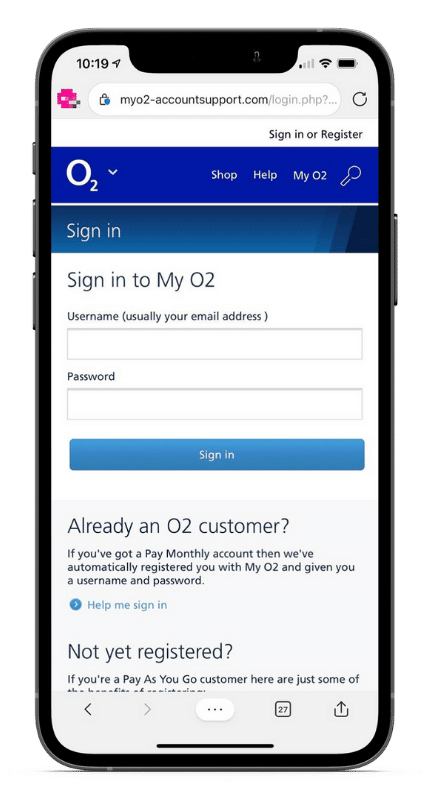
Don’t let BYOD stand for Bring Your Own Disaster
Mobile phishing attacks that target individuals can quickly compromise an organisation. That’s because more people are using their personal phones for work. The pandemic accelerated that as most people began working from home. Suddenly the phone you use to access your work emails is the same one you use to surf Facebook or play games on.
75% of phones in the enterprise will be BYOD
Gartner
Mobile Device Management (MDM) is often used by businesses with BYOD and COPE mobility strategies, but it doesn’t actually provide threat detection and remediation. But add MTD to detect any potential phishing risk and you have a powerful combination allowing IT teams to block access to particular business content or systems if there is a threat.
Find out more about how different mobile solutions fit together.
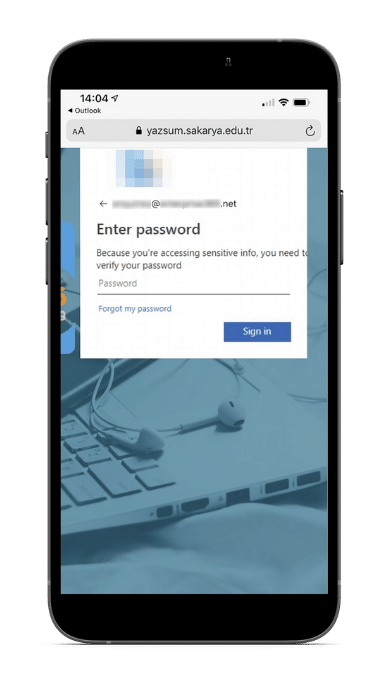
A mobile phishing attack can devastate your company
The ripple effect of a single successful data breach can quickly escalate. Here are just a few of the risks:
- Credential theft: Entering access credentials for on online account can give attackers access to it, and potentially others, if victims reuse passwords.
- Device compromise: Phishing attackers can infect mobile devices with malware that steals data from the phone and uses the device to target contacts, spreading the attack.
- Business Email Compromise (BEC): Phishing attackers have been spotted impersonating executives and using SMS messages to target administrators, asking them to wire money to fraudulent accounts. One successful attack can cost millions.
- Ransomware infections: All it takes is a compromised company account to spread a ransomware attack internally among employees.
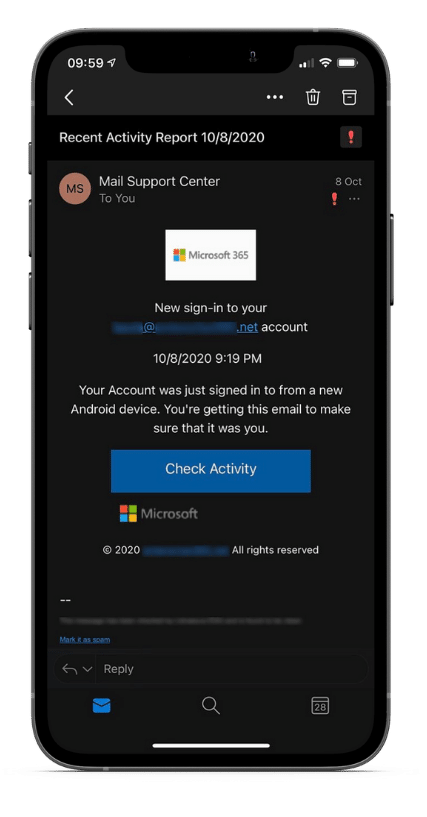
How does mobile phishing work?
Phishing used to be an email-only activity until smartphones came along. Now, as smartphones are used for both work and personal activity, your employees need to be aware of the different ways that cybercriminals target victims.
- An email opened on a mobile can make phishing harder to spot. Smaller screens make it more difficult to see who really sent the email. This, coupled with the fact that we often use our mobiles when multi-tasking, makes it easier to fall prey to.
- An SMS, WhatsApp or social media message is a common method of attack for mobile phishers, especially if the message appears – at first glance – to be from a known brand or someone the victim expected to get a message from. Read more about SMS phishing and a recent WhatsApp phishing (whishing) scam.
- Malicious mobile apps downloaded from official app stores have impersonated software from well-known online services, displaying login screens that collect your personal account details. If this happens, you might never even realise you’ve been phished.
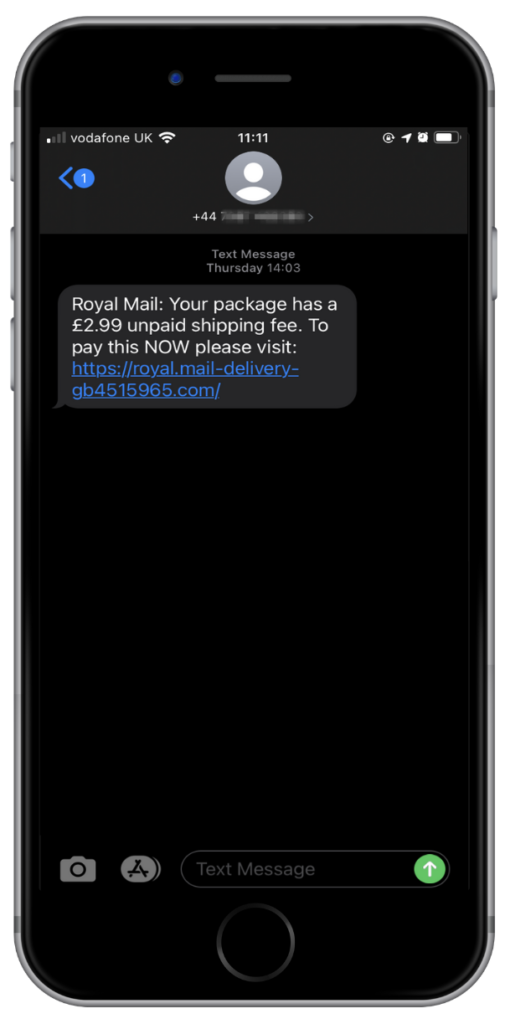
Mobile phishing is more dangerous
The majority of employees have their company email account on their mobiles. Although the general population are becoming more mindful of email phishing, when it happens on a mobile phone, it can be a lot harder to spot. Why?
- It catches you off-guard when you’re distracted.
- It arrives on tiny screens that people don’t read properly.
- It targets devices that aren’t protected by your company network.
Coaching staff on how to spot suspect emails is very useful when applied to desktops. Unfortunately, the same strategies don’t apply to mobiles, as the advice to ‘hover over a link to see where it goes before clicking on it’, is a redundant exercise on a mobile device, so it’s important to update your security training.
How we can help
All the images above are examples of real phishing scams we’ve seen on mobiles.
Any business that uses mobile devices has a duty to its customers to make sure they are doing everything in their power to protect against threats such a mobile phishing.
A simple and effective way to do so is with Trustd MTD. Quick and easy set up, you can enrol your organisation’s devices within five minutes to protect BYOD, COBO or COPE devices from phishing and other malware, credential theft via compromised WiFi, device vulnerabilities, and malicious web and app content.
Trustd works directly on smartphones to spot known phishing links and warn users before they give up their details. We use powerful AI techniques to look for suspicious patterns in web addresses, backed up by lists of known phishing URLs.
Free download

Try it for yourself
Trustd is a new mobile threat defence solution that is quick and simple to set up – see for yourself with our 14-day free trial. Get set up in 5 minutes. If you’re looking for our free Trustd app, head over here.