Mobile Security for the Recruitment Sector
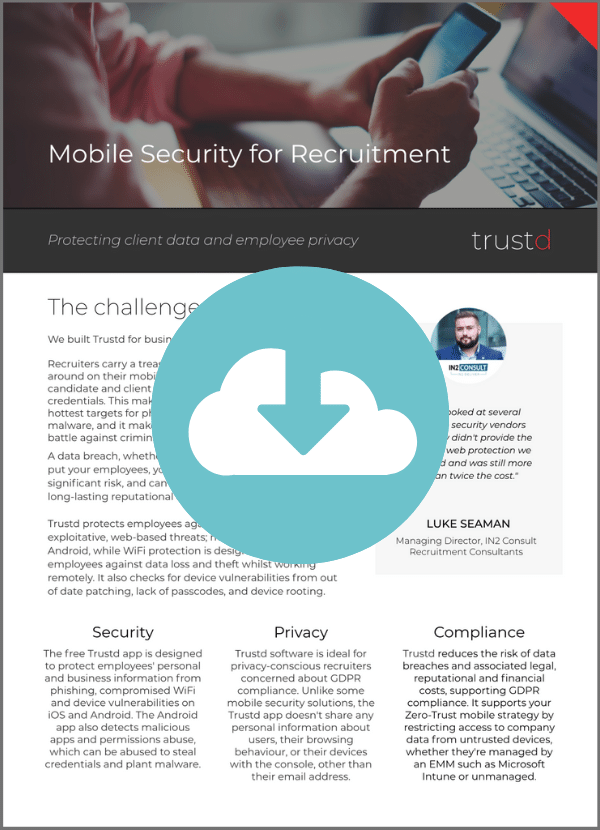
Recruiters’ phones and tablets are hot targets for phishing attacks and data theft, and need security software just like laptops and computers do.
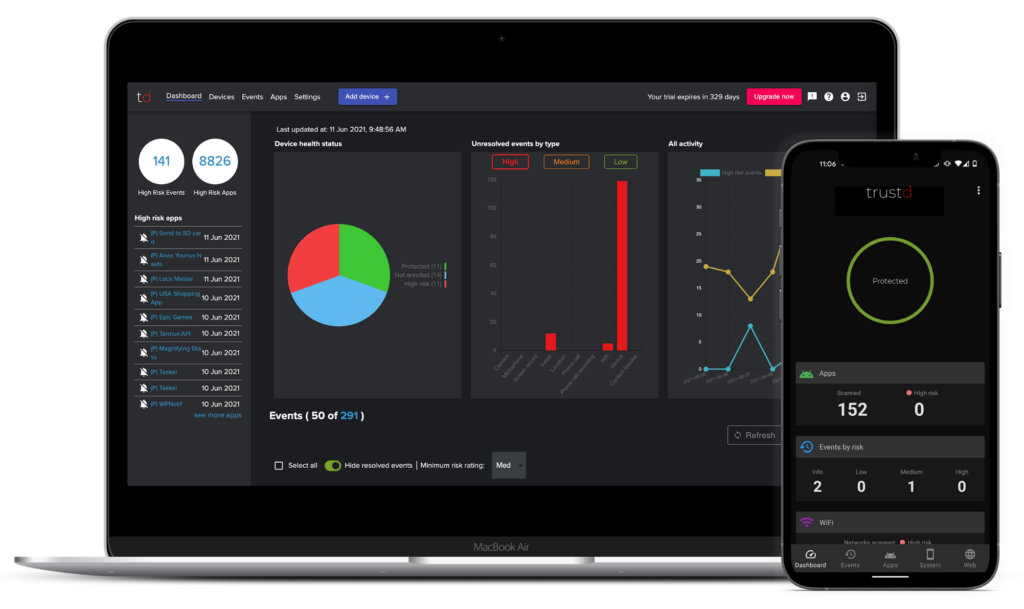
The combination of the Trustd apps on your phones and the Trustd MTD console to monitor compliance, protects your phones, protects your clients’ data, and guards against GDPR violations. It doesn’t cost the earth and you don’t have to be a rocket scientist to use it.
Security
Trustd’s software is designed to protect employees’ phones from phishing, compromised WiFi hotspots, device vulnerabilities, permission abuse, and other threats.
Privacy
Unlike some Unified Endpoint Management (UEM) solutions, the Traced app doesn’t leak any personal information about its employees, their browsing, or their devices, to the company they work for, making it perfect for a “Bring your own device” (BYOD) environment. Employee privacy is our top priority.
Compliance
Working together, the Trustd app and the console provide a sophisticated, low cost Mobile Threat Defence (MTD) solution that can detect and analyse threats to your business, prevent data breaches and ensure compliance.
Other vendors didn’t provide the WiFi or web protection we needed, and was still more than twice the cost.
Luke Seaman, IN2 Consult
Traced for recruitment
Recruiter case study
Recruiter data sheet
Start a free trial now and secure up to 5 devices
See how quick and easy it is to get going. You don’t need a credit card, you just need 2 minutes. Register here for your Trustd MTD account, download the app to your phone or tablet, sync them up – and you’re done.
In 5 minutes’ time you’ll know that Trustd has checked your device for threats and you can see the risk status on the dashboard.
Start a 2-week free trial now. No credit card required.
Now imagine if you had that level of protection on the phones of everyone in your organisation? And, could see whether those devices were safe or at risk? You’d significantly reduce your risk of a data breach, and could demonstrate compliance with regulations that require you to keep personal data safe.