Your one-stop guide to mobile security acronyms and how the solutions fit together
The tech industry loves acronyms. Analyst firms thrive by defining new ones to describe complex product subcategories. It can be difficult for customers to keep up, especially in a fast-evolving space like mobile device security.
Understanding mobile security acronyms has never been more crucial because mobile device security has never been more important. Smartphones and tablets are especially vulnerable to cyber-espionage, which can affect large and small organisations alike.
Mobile devices have been the most compromised assets after desktops in cyber-espionage cases since 2014, according to the Verizon Cyber Espionage report, beating laptops. Security company Trend Micro says that mobile cyber-espionage attacks increased by a stunning 1,400% over past four years. If you’re still not convinced, ask Jeff.
Getting the right kind of security for your business means knowing the difference between MDM, EMM, UEM, and MTD. We’re here to help you deconstruct it, see how they fit together, and understand where Trustd’s mobile threat defence fits in.
Mobile Device Management (MDM)
Perhaps the most common mobility product, MDM focuses on device management alone and can provide some minimal security through policies (in the same way that Active Directory can for Windows devices). After installing it on a mobile device, you can apply policies which might do things like block access to the camera, or enforce internet access through a VPN. You can also use MDM systems to remotely lock or wipe a device.
Enterprise Mobile Management (EMM)
MDM is the least functional solution because it focuses on the device rather than what runs on it. EMM fills that gap by offering everything MDM has, along with a host of extras covering more of the mobile device’s data and application ecosystem. That comes with a gaggle of other acronyms.
EMM often features mobile identity management (MIM) services, also often known as identity and access management (IAM), for better authentication of users and their devices. It offers mobile application management (MAM) for managing the enterprise software installed on the device, often along with its licences. EMM solutions also usually include mobile content management (MCM) for securing content on the device using encrypted containers that separate work and personal data. Then there’s mobile expense management (MEM) for tracking data usage.
Unified Endpoint Management (UEM)
EMM expands mobile device management to embrace more of the device’s ecosystem, but it only addresses the two mainstream mobile operating systems, iOS and Android. UEM extends EMM’s coverage to include laptops, smart devices and other computers.
Mobile Threat Defence (MTD)
All of the solutions above focus on enabling administrators to manage device security but they stop short of protecting the devices themselves from attack. It’s all very well ensuring that only authorised devices can connect to your network or access your email system, but what if malware running on that device enables an attacker to control its camera, spying on sensitive meetings in secret?
That’s where Mobile Threat Defence (MTD, although it’s sometimes called Mobile EDR) comes into play. It uses threat intelligence to discover threats and attacks that might be missed by any of the policies which you have in place, whether that be your MDM policy right through to the MTD detection engine.
MTD focuses on detecting and remediating existing attacks, often using automated prevention. Trustd is an MTD solution that uses deep learning techniques that spot and stop unusual device or app behaviour, heading off attacks on the device while alerting users and admins to dangers in their digital surroundings like insecure WiFi networks.
MTD not only protects against threats like malware and phishing emails, but also detects behaviour that could indicate an attack. That includes permission abuse from apps that access the phone’s microphone or camera in the background without the user’s knowledge.
It can also spot and stop attempts to disable the phone’s security features such as Google Play Protect, which checks an app’s safety before downloading it from the Google Play store. This prevents apps from gaining a foothold on a device by changing the underlying platform.
You may think that you’re covered completely with an MDM or EMM solution, but after unpicking the mobile security industry’s verbiage you might find that you need more than simple configuration management. MTD complements these other options to offer extra protection at a time when the stakes have never been higher.
But what do they all do?!
The only way to really make sense of the terms is to look at them side-by-side and compare what they actually do.
| MDM | EMM | UEM | MTD | |
|---|---|---|---|---|
| Threat detection | ||||
| Remote visibility of high risk devices | ✔ | |||
| Malicious app detection and analysis | ✔ | |||
| On-device protection from phishing | ✔ | |||
| WiFi Man-in-the-Middle attack detection | ✔ | |||
| Software vulnerability detection | ✔ | |||
| Security Management | ||||
| Analyse apps on devices | ✔ | ✔ | ✔ | |
| Block unwanted apps or websites | ✔ | ✔ | ✔ | |
| Enforce device encryption and password | ✔ | ✔ | ✔ | |
| Device management | ||||
| Remote lock or wipe | ✔ | ✔ | ✔ | |
| Apply access and usage policies to devices | ✔ | ✔ | ✔ | |
| Enforce use of VPN | ✔ | ✔ | ✔ | |
| Identity and Access Management | ||||
| Manage access to corporate resources | ✔ | ✔ | ✔ | ✔ |
| Enforce MFA and strong passwords | ✔ | ✔ | ✔ | |
| Authenticate network services with certificates | ✔ | ✔ | ✔ | |
| Expense management | ||||
| Track and audit expenses and data usage | ✔ | ✔ | ||
| Content Management | ||||
| Force encryption on business data | ✔ | ✔ | ||
| Manage content sharing and access | ✔ | ✔ | ||
| Application Management | ||||
| Containerisation of personal and work data | ✔ | ✔ | ||
| Control access to apps and data | ✔ | ✔ | ✔ | |
| Deploy and update app remotely | ✔ | ✔ | ||
| All device management (including desktops, laptops, phones and tablets) | ||||
| Manage *all* your endpoints remotely | ✔ |
In summary…
MDM, EMM, and UEM give you more or less control over a device but doesn’t detect threats.
MTD actively detects threats, as you can see here:
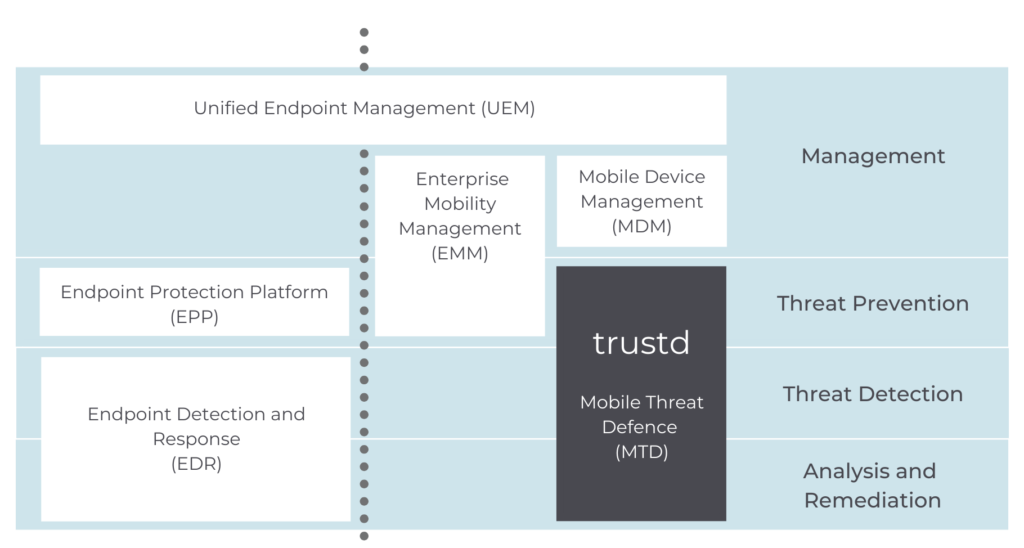
So you want to ensure you have MTD as well as the management solution that best suits your organisation.
Try it for yourself
Trustd is a new mobile threat defence solution that takes 5 minutes to set up – see for yourself with our 14-day free trial. If you’re looking for our free app, head over here.