Trustd supports Zero-Trust for mobile devices, whether managed by an MDM/MAM or not – in a single solution.
Trustd provides conditional access to business resources, blocking a mobile device until that device verifies itself as trustworthy.
Zero-Trust helps to prevent data breaches
As more employees work outside the perimeter – from anywhere, on any device and on any network, businesses need a security model that supports this new operational efficiency. The traditional perimeter model poses challenges for organisational security, exposing your company to the risks from malware and data breaches from IT devices that are unknown and unsafe.
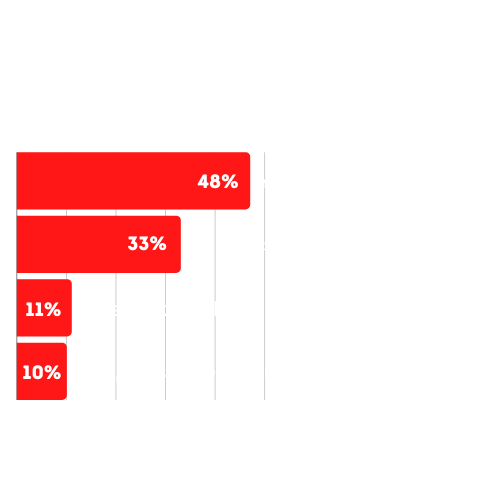
83% were concerned about the growth of “shadow IT”
Verizon Mobile Security Index 2021
Zero-Trust inherently distrusts any device or network until they are authenticated and proven to be safe. One method of enforcing Zero-Trust principles on mobiles is by blocking access to business resources from devices that have not been verified as trustworthy.

The benefits of Trustd for Zero-Trust
Charlie Gero at Akamai Technologies recognises how important Zero-Trust has become. “If you want to stop breaches, Zero-Trust is the best way how.”
Here are just a few of the benefits of using Trustd’s conditional access capabilities in your Zero-Trust strategy:
- Reduces the risk of data breaches, fines and damages from cyberthreats.
- Enables secure remote working without compromising efficiency.
- Automatically allows access to company data when a user’s device is validated as trusted, and restricts access if it becomes untrusted.
- Protects your private data on mobiles, anywhere and on any network.
Supporting Zero-Trust
4. Use policies to authorise requests
Each request for data or services should be authorised against a policy. The power of a zero trust architecture comes from the access policies you define.
Zero trust architecture design principles
There’s no need for bolt-ons, premium licences or third-party software. Trustd’s unique approach to Zero-Trust means that Trustd protects devices and restricts access to company data for untrusted devices whether they are enrolled in an MDM/MAM or not, in a single solution.
This makes Trustd the ideal choice for organisations that want to provide a secure BYOD or COBO/COPE environment, while ensuring employee privacy.
Free Zero Trust white paper
We explain how Zero-Trust for mobiles works in practice, as well as how Trustd is unique in its approach. Download now.

We’re members of MISA
Trustd’s integrations with Microsoft Entra ID and Microsoft Intune help customers to achieve compliance and mitigate the growing business risks of cyber attacks and data breaches originating from company and personal mobile devices.
See how we achieve Zero-Trust through integration with Entra ID
