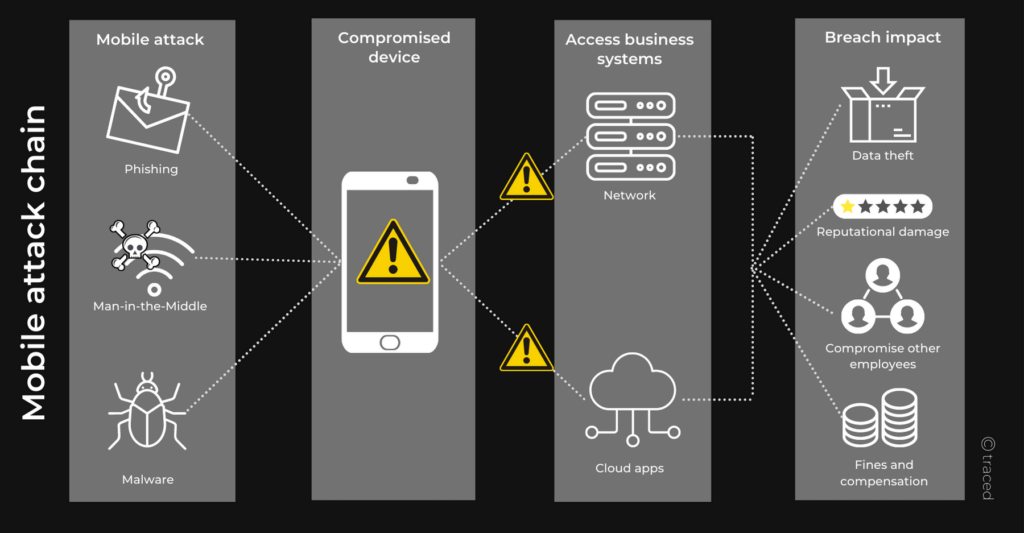
How mobile-borne threats like phishing and malware end up on business networks, leading to costly data breaches.
If you’re wondering whether mobile devices actually pose a cyberthreat to your business data, or whether it’s just a lot of vendor hype… you’re not alone.
In reality, as with most things in life, it’s not black and white, and it largely depends on your particular mobility set up as to whether you believe mobile security to be a priority for your IT budgets.
Let’s look at some of the threats, their prevalence, whether you actually need to worry about them, and the best way to mitigate them.
Firstly, how can mobile threats on personal phones impact businesses?
This diagram summarises the chain the attack from mobile threats, all the way through to the impact on your business.
- Quite simply, it starts with a cyberthreat – often unique to mobile devices – such as phishing, malware (like spyware, viruses, keyloggers, banking Trojans etc) or Man-in-the-Middle attacks.
- The attackers can then either login to phishing victims’ user accounts remotely, get data back from compromised devices or even remotely access those devices. So when the user connects to their business network or accesses Cloud apps like Google Drive, Slack, etc from their smartphone any data that resided on those systems is now potentially in the hands of the attacker.
- This constitutes a data breach, and can result in theft of data, regulatory fines, compensation payouts to customers, personal information that can lead to cyberattacks on other employees, and reputational damage.
But, how likely are these sorts of mobile attacks?
Well, that depends on a few factors, including your sector and your mobility environment.
For example, if you’re a big organisation that works with a lot of valuable financial data about customers, then you can assume you’re a hot target for cybercriminals. Attackers might spend a lot more effort on social engineering to try to con employees into divulging passwords, or opening malicious attachments.
If you run a local chain of hair salons, you still have personally identifiable information (PII) on your customers, including perhaps contact details, payment information, medical data…
In this second instance, you’re more likely to be subject to a scattergun approach to cyberattacks rather than a targeted Spear-phishing or Whaling attack – mainly because it makes better economic sense for cyberattackers to use cheaper attacks on more organisations, and invest more time and effort into those where the rewards are greater.
Furthermore, if your employees are high risk targets for cyberattackers you might decide to prevent access to any business systems from personal smartphones, and provide company-owned devices instead. Or insist that any devices used for work have MDM and/or MTD installed on them so you can manage access and apps, and detect threats to your business before it can have an impact.
Mobile threats increased 1,400% in the four years between 2016 and 2020
Apps – and Apple vs Android
Whether your employees use Android or iOS is another consideration. Because of Apple’s walled garden it’s much harder for people to install “non-approved” apps on an iPhone – all apps need to be first vetted by the App Store, and the rules around privacy and security and stringent.
That’s not to say that Android is less secure than Apple, and bad apps occasionally make their way on to the App Store just as they on the Google Play store – they just crop up more often on Google Play. Android is also more configurable, so it can be left vulnerable if users aren’t comfortable with setting it up well, while Apple takes that out of users’ hands.
Apple Blocked 1.6 Million Risky, Vulnerable Apps in 2021
https://www.securityweek.com/apple-blocked-16-million-risky-vulnerable-apps-2021
Apps can be created malicious or can become compromised over time, but if your mobility environment is primarily Apple you don’t need to worry so much about malware from apps. Make sure your employees aren’t rooting their devices though to allow them to install apps from non-official sources.
Malicious apps install spyware or keyloggers that harvest data from your device – such as taking screenshots or screen recordings of login details. They can forward any passcodes or security verification information to the attacker. They can spread to friends, family and coworkers via accessing the address books and sending text messages from your device. Read our article about bad apps to understand more about what malicious apps can do.
Compromised WiFi networks
Man-in-the-Middle attacks occur over public WiFi networks that have been compromised. Attackers sit “in the middle” – intercepting any data that flows over the network, including passwords, emails, contact information, and more.
Traced researchers found 1 in 20 public networks had an active Man-in-Middle attack happening
Traced, 2020
Attackers can use this information to log directly onto your accounts using your credentials, or to conduct social engineering attacks on friends and co-workers by using the information they’re harvested from your device to trick them into clicking a phishing link or parting with passwords or other sensitive information.
Watch an active Man-in-the-Middle attack happening on a device.
Text phishing attacks
Phishing has been around long enough that we’re all familiar with the tricks and probably don’t fall for email scams very often at all.
However, mobile phishing is an entirely different beast – small screens, minimal information in text messages, easily spoofed details, and a lack of focus on the users’ part means it’s far easier to be duped by mobile phishing.
You’ve probably received a fair few Smishing (SMS phishing) messages yourself – ever been asked to pay a nominal fee for a parcel delivery? Or been asked to re-verify your login details on your banking website as part of routine security practices?
Read more about mobile phishing in “It Started With A Phish”

What’s the best way to protect against mobile threats?
There are different types of mobile security solutions available – ranging from management solutions like EMM and MDM to threat defence solutions like MTD. The good news is that you can layer these solutions on top of each other as your business grows or your mobility environment changes.
This table shows what the different solutions can do, and you can see how they can be layered to achieve greater levels of management. The most important thing to note though is that mobile management solutions don’t offer any threat detection or remediation – only MTD (Mobile Threat Defence) does that.
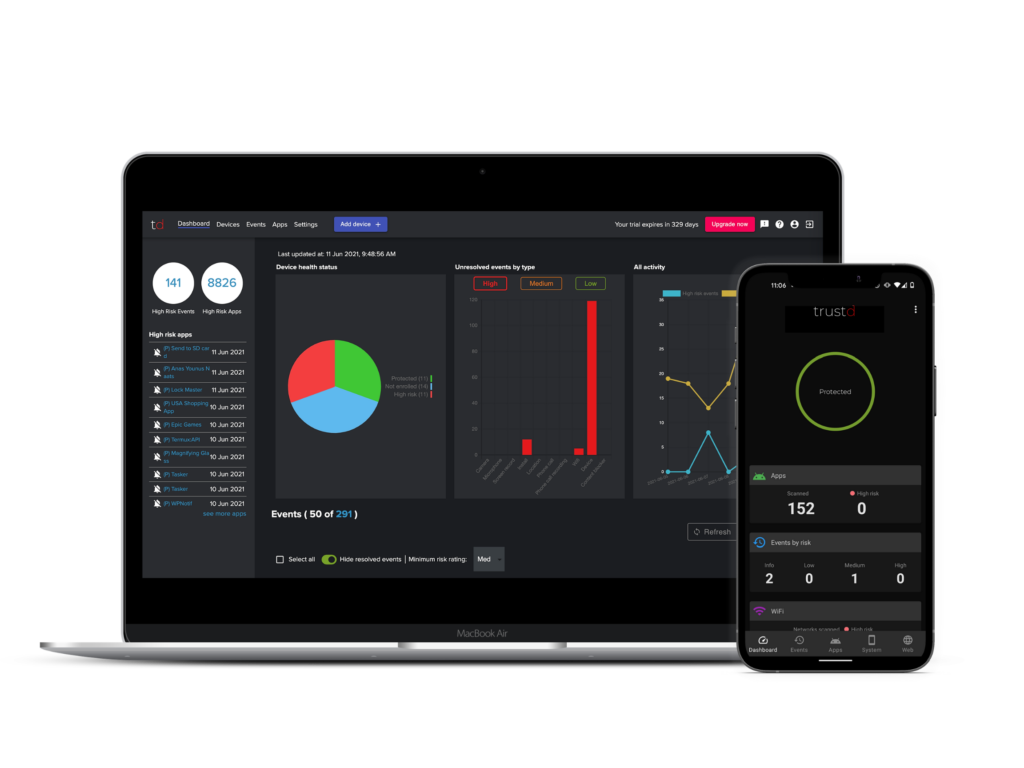
We’ve found that smaller, less complex businesses prefer to start with an MTD like Trustd, which has a low-cost per device, supports iOS and Android, blocks phishing, detects malware and compromised WiFi networks, provides alerts for unpatched or rooted devices, and ensures absolute user privacy. The administrative console is intuitive and it’s easy to enrol new devices, so you have visibility over the threat status of each employee’s device, but not access to any browsing history or app usage.
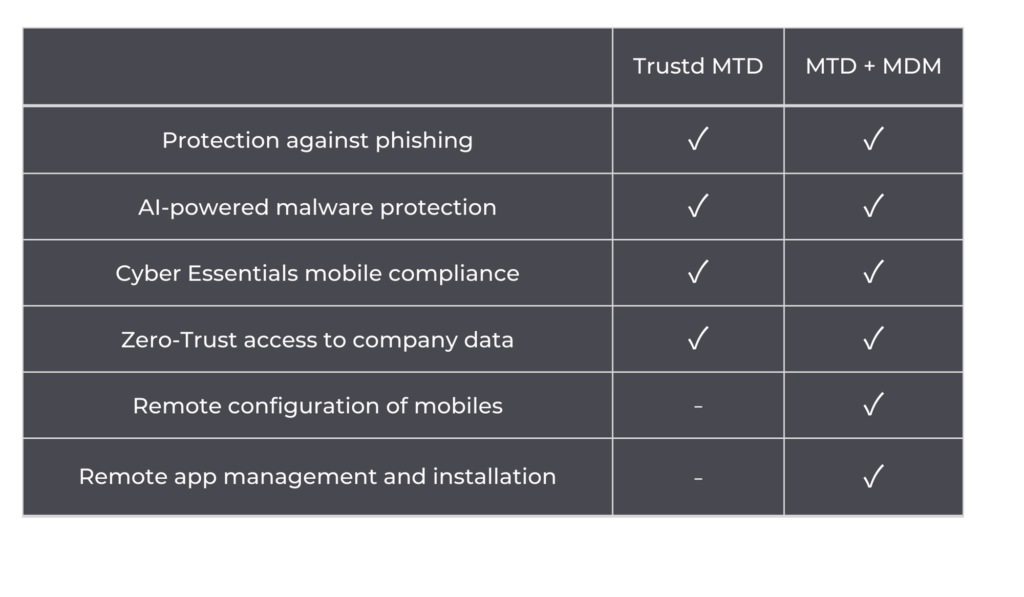
As businesses grow, many add MDM or EMM, so that they can manage personal and corporate mobile devices more efficiently. Trustd MTD can integrate with most management solutions, such as Intune, SOTI, AirWatch, or Meraki for easy deployment, threat detection and remediation that doesn’t come with MDM or EMM, and to provide Zero-Trust access to business apps.
Try it for yourself
Trustd mobile threat defence solution takes 5 minutes to set up – see for yourself with our 14-day free trial. If you’re looking for our free app, head over here.