Researchers at ThreatFabric are warning people about a new Android malware-for-rent. “Hook” is a variant of banking Trojan family ERMAC, remote access and device take over capabilities.

Hook is created and rented released by the threat actor behind the original ERMAC banking trojans, DukeEugene, and is understood to be basically a re-brand of the existing product, with a few important modifications.
The Hacker News reported:
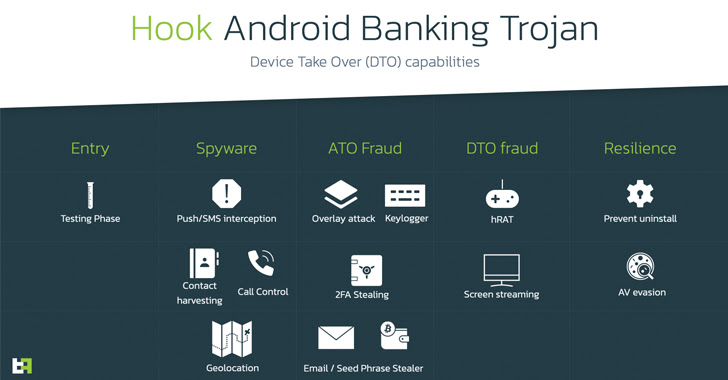
“Like other Android malware of its ilk, the malware abuses Android’s accessibility services APIs to conduct overlay attacks and harvest all kinds of sensitive information such as contacts, call logs, keystrokes, two-factor authentication (2FA) tokens, and even WhatsApp messages.”
New RAT capabilities
The primary development is the addition of Remote Access Tool (RAT) capabilities, which uses Android’s Accessibility Services to interact with the different UI elements required to perform a wide range of operations – including screenshots, clicks and swipes, filling text boxes, sending messages, and downloading images from the device.
According to ThreatFabric researcher Dario Durando:
“Device Take Over (DTO) [is] the fraud methodology that is most likely to be successful and not detected by fraud scoring engines or fraud analysts. This is most likely what triggered the development of this new malware variant.”
Hook can be delivered via phishing campaigns, spoof apps, Telegram channels, or via Google Play Store dropper apps.
To conclude, the ThreatFabric report states:
Hook now joins the very dangerous ranks of malware which is able to perform a full attack chain from infection to fraudulent transaction. In addition, it includes new capabilities typical of spyware, which allow criminals to track and spy on the device, gaining full visibility not only on the banking details of the victim, but also messaging, geolocation, and control over files present on the phone.