With most people using mobile devices for work in some form, you really don’t want malware like last month’s FluBot on your device.
In April, Android users were attacked by a new viral threat that swept the UK and infected phones by the thousand. Called FluBot, it spread by sending phishing messages via SMS texts.
We call that smishing, and it’s surprisingly effective because it’s just so hard for people to spot scam texts from the real deal.
FluBot is malware that steals passwords, contact details and more from Android devices, and then uses those contact details to spread to other devices. It fools people into installing it by sending a message warning that they’ve missed a parcel delivery, and directs them to download a tracking app, which is of course nothing more than another FluBot download.
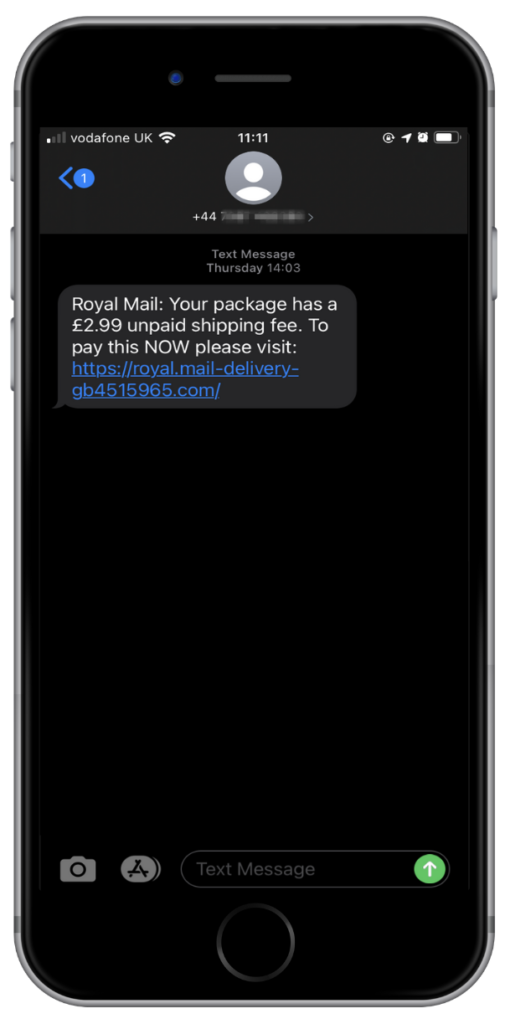
We saw fake texts pretending to be from Royal Mail, Amazon and DHL.
The FluBot-carrying app also asked for access to the victim’s phone book and for permission to read and send SMS messages. In fact, it makes itself the default SMS application on the victim’s phone. This is what enabled the malware to spread so quickly.
Infected phones send stolen contact lists to the attacker’s server, which then redistributes them to other infected phones, creating a kind of distributed criminal call centre. It forces those phones to send more phishing texts, spreading the load between them to fly under the radar.
FluBot was especially dastardly because it also used its accessibility privileges to deactivate Google’s Play Protect feature, which monitors Android for suspicious software activity. It even stopped the user deleting it.
This was a sophisticated piece of malware with roots as a banking Trojan. ThreatFabric first discovered it at the start of the year (read its report here), and Proofpoint found the English language version of the malware almost exclusively targeting UK users. At the end of April, around 7,000 devices were spreading the campaign throughout the UK, with smishing texts hitting tens of thousands per hour. Many of the messages pretended to be from DHL, although some victims have also reported fake texts from the Royal Mail. The problem became so serious that the National Cyber Security Centre even published a warning about it.
An app that sends employee login credentials and business contacts’ personal information to a data-harvesting server isn’t something your employees want on their phones. So how do you help them avoid it?
How to protect employees from SMS phishing
Third-party application protection is especially important when dealing with smishing. The Traced app protects Android users in several ways.
Our machine learning engine uses natural language processing to spot any suspicious language in links in emails, messages and texts.
We also check URLs to see if any suspicious activity has been associated with them so that we can warn users. That helps keep smishing software like this off their phones in the first place.
Our iOS app works in a slightly different way – blocking webpages that we deem to be malicious from loading in the Safari browser.
In the unlikely event that the software makes it onto a phone protected by Traced, our MTD (mobile threat defence) software, Traced Control, will alert administrators that something is up, enabling them to work with the user to eliminate the threat.
With malware epidemics like this one developing and spreading so quickly, both official work phones and employee-owned BYOD devices are at risk. Effective mobile threat defence is a good way to protect yourself against a digital cold that you really don’t want to catch.